Cyber threats are very real and exploited vulnerabilities are still the root cause of most IT security breaches. Regular ‘vulnerability’ scanning and remediation to detect and defend your network against the threats from hackers should, therefore, be part of your IT Security…
Staff bringing their own mobiles to work may be convenient but it can also put your company at risk. Watch our video and download our free brochure on how you can protect your data and staff at work.
For companies that use Office 365 and have multiple office locations, a mobile workforce or a number of employees, being able to control email signatures for all users, in one central location, is a very attractive proposition.
Data theft has become big business, either stealing it, or locking it and charging a fee for its release. And unfortunately you can no longer sit back and be complacent.
In preparation for the changes to the data protection law which come into effect next May, your company could benefit from Cyber-Security accreditation as a first step to becoming compliant.
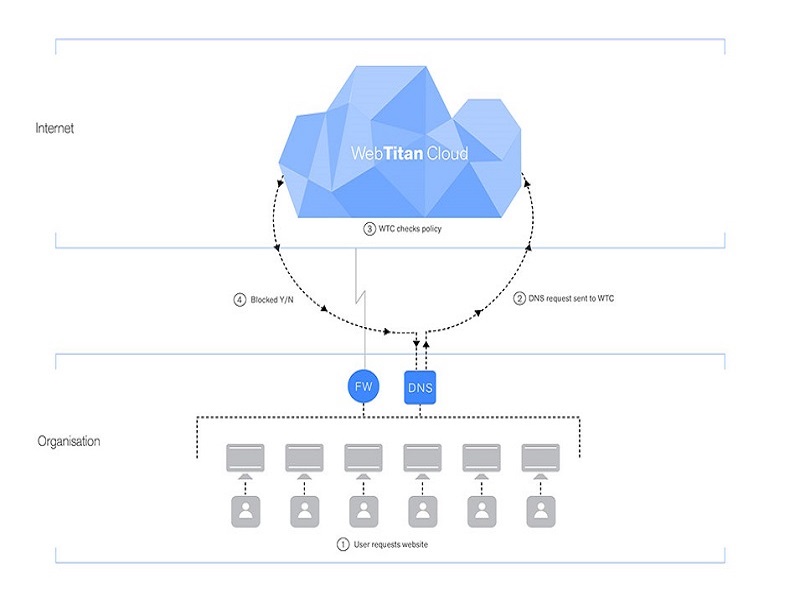
The best way to stop undesirable threats and unwanted content from affecting your IT systems is to detect them in the Cloud. One way to achieve this is ...